Back in 2021, Kerberos support for Azure AD was available as a preview. A lot has happened since then and the three-headed hellhound continues to make its way and shake up the cloud. This article is a collection of information on what Azure AD with Kerberos and Azure Files already provides and where the journey will go. This is because support for Azure Files with Kerberos has also recently been publicly communicated, although at the time of writing this article it is still in preview.
History of Azure Files and Kerberos Support
To help you understand, let me first present the background history of Azure Files and Kerberos as a short form.
Note: The following points serve as an overview. For further information on the points mentioned, links are provided in each case for further reading.
Azure File Sync
Azure Files has been available for quite some time. For a long time, one or more on-premises file servers could be synchronized using Azure File Sync. With the cloud tiering of Azure File Sync, organizations gained the ability to save expensive and unnecessary on-premises storage space and obtain it in the Azure cloud without sacrificing data. This construct is particularly effective in multi-site scenarios, where Azure Files is the central hub and only necessary data is written to the respective sites.
Azure Files identity-based authentication
With identity-based authentication, Microsoft creates new possibilities for Azure Files. This allows authentication to be configured on the Azure File Share via an available Active Directory. Users that exist in Active Directory and are synchronized into Azure AD can thus access the Azure Files fileshare, provided they are authorized. However, the client must belong to the classic domain and authenticate to it.
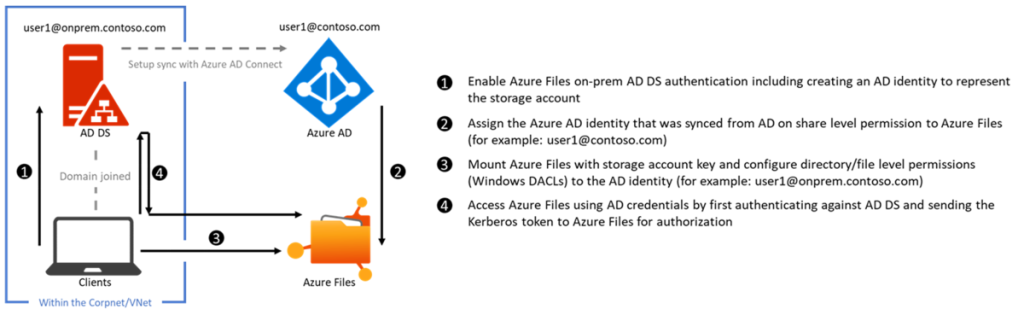
Supported are on-premises AD DS and also Azure AD DS.
Azure Files Identity Based Authentication
Azure AD Kerberos Support
One of the most mentioned main differences between Azure Active Directory (AAD) and a classic Active Directory has been that Azure AD does not support Kerberos. But at the end of 2021, Microsoft announced the preview of AAD Kerberos support. Gradually, AAD has gained more and more Kerberos functionality. For example, single sign-on (SSO) access to on-premises resources can now be granted via Azure Active Directory, along with a classic Active Directory. The AAD can therefore issue partial Kerberos ticket-granting tickets (TGTs).
You can find out how this works at this Link.
Highly recommended is the Tech Community article: Deep dive: How Azure AD Kerberos works
Kudos to John Savill for explaining AAD Kerberos Support in a video, clear as ever.
Ankündigung: Azure Files und Kerberos Support
The Azure Files and Azure AD cloud story continues apace. On August 30, 2022, Microsoft announced the next scoop with Azure AD Kerberos Support for Azure Files Identity-based Authentication. This preview feature, in combination with Azure AD Kerberos Support, now allows Azure AD identified users to connect to Azure Fileshares without any line of sight to the classic domain. For this to work, clients must be Azure AD joined (AAD join), or hybrid joined (hybrid join). The requirement of a classic domain connection is thus completely eliminated, while the user accounts still need to be synchronized.
Microsoft Announcement: AAD Kerberos and Azure Files
In the following video, I show how to enable Azure AD Kerberos for Azure Files in just a few steps.
Restrictions and the journey to the cloud only file server
In my eyes, the latest announcement of Azure Files and Kerberos support is great news and a big step towards the future. However, Microsoft is not quite at the end of the journey to the cloud only file server yet. The following limitations still exist, among others.
SMB Port Blocking
In order to access the fileshare, the connection must be granted via the SMB port (445). Many ISPs block this port by default. Access via the Internet in today's mobile world is therefore usually only possible via VPN. Thus, the dependency of a site-to-site and / or point-to-site VPN to connect to Azure Files still exists. It can be assumed that this hurdle will be removed sooner or later by Windows 11. Currently, a workaround can be implemented with SMB over QUIC with additional infrastructure.
Cloud Synchronisierte Benutzer
At this time, only synchronized users can access the fileshare. Only users existing in the cloud (cloud only) cannot access it. This is probably due, among other things, to the fact that Azure AD cannot yet issue full-fledged Kerberos ticket-granting tickets (TGTs), but only partial ones. An existing Active Directory environment is therefore still mandatory and prevents the true cloud only file server. Microsoft is striving to ensure that this requirement will also no longer exist in the future and that a fully-fledged cloud only file server will be possible. However, due to the complexity, no time line is known on the part of Microsoft.
I am convinced that soon the next news will follow, which will bring us step by step closer to the goal of a full-fledged cloud only file server.
Azure Files and Kerberos Support - The Cloud Story Continues. Stay tuned.
Sources:
https://learn.microsoft.com/azure/storage/file-sync/file-sync-introduction?WT.mc_id=AZ-MVP-5004129