Over the Easter weekend of 2025, many organizations using Microsoft Entra ID (formerly Azure AD) were caught off guard when a significant number of users were suddenly blocked from accessing corporate resources. The cause? Entra ID categorized these accounts as “high risk” due to “leaked credentials”. Conditional Access Policies blocked these users from attempting access due to the existing risk. In this post, I'll explain what happened, why it happened, and most importantly, provide a simple and secure solution to the problem.
What happened?
Golem.de reports that on April 20, 2025, between 6 a.m. and 11 a.m. German time, numerous Entra ID users were blocked due to incorrect logging of refresh tokens. Microsoft had inadvertently logged the refresh tokens of the affected users, which led to security warnings and the blocking of the accounts. Administrators received warnings about allegedly leaked credentials, which led to the immediate suspension of the affected accounts. [Source1]
Many organizations have policies such as “block access if user risk = high” (a best practice!), which have been triggered en masse as a result.
Cause
According to whispers, this is a problem with a new enterprise app. The rollout by Microsoft of “MACE Credential Revocation”, which is intended to provide enhanced protection against “leaked credentials”, has increased the user risk accordingly, probably due to the logged refresh tokens. Microsoft has not (yet?) publicly confirmed the cause.
Risk assessment
First of all, there is no need to panic, as the blocked users do not pose a risk. But even if it is a mistake on Microsoft's part and the logged refresh tokens probably cannot be viewed by a human, this incident should still be taken seriously and treated with appropriate caution. This is because refresh tokens are valid for a longer period depending on the tenant (default = 90 days) and also contain information on MFA authentication. The correct reaction is therefore important.
Solution for restoring user accounts
If your users are still locked out or you want to prepare for similar incidents, I recommend the following procedure:
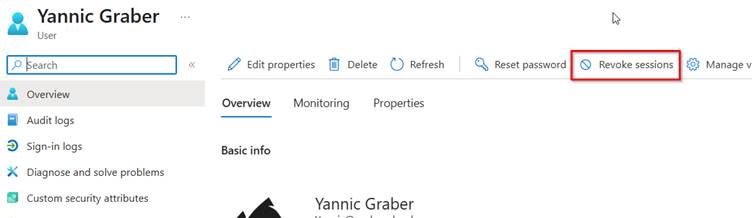
1. revoke user sessions
Why: If login data is leaked, active sessions may be at risk.
How: Go to https://entra.microsoft.com for the affected user and click on Revoke sessions. Dadurch wird der Benutzer sofort von allen Geräten und Sitzungen abgemeldet.
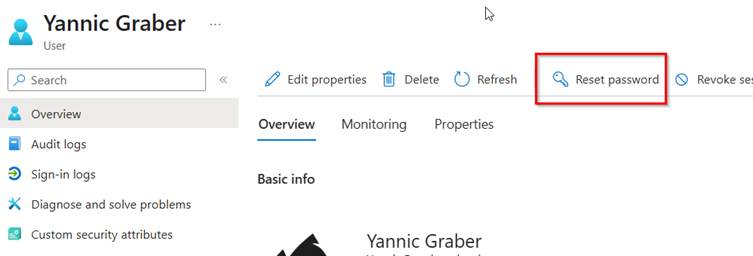
2. reset the user's password
Why: Ensure that all leaked or compromised access data is no longer valid. Even if, in this case, this is not the case. Safe is safe.
How: For cloud-only users, select the Reset password option in the user's profile. The user will then receive a temporary password that must be changed the next time they log in. In the case of synchronized users, the password reset is easiest to do directly in the on-prem AD.
3. remove the user risk status
Why: Users who are flagged as high risk remain blocked by access control until their risk has been eliminated.
How: In the Entra Admin Portal, navigate under Identity > Protection to Identity Protection > Risky users and select the affected user. Click Confirm user safe (if you have checked the identity of the user and are sure that there is no real risk).
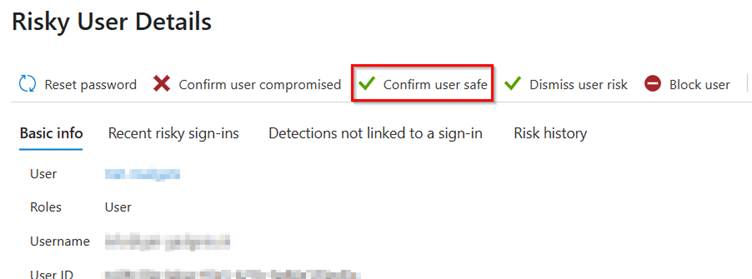
This removes the “High risk” flag and the Conditional Access Policies allow you to log in again.
4. communication with end users
As a final step, inform the users about the incident and the measures taken. Advise them to watch out for phishing attempts and report any suspicious activity.
Note: It has happened with cloud-only users that the user did not have to change the password directly when logging in for the first time (see 2. Resetting the user's password). So make them aware that they may have to do this manually themselves or accompany them directly.
Conclusion
Microsoft Entra ID's risk-based controls offer a powerful and effective tools for protecting your users. However, nothing is flawless and therefore careful coordination is required, as well as a certain acceptance of false positives and their consequences. Incidents like this show the importance of multi-layered security and a well-thought-out response plan in order to be able to react quickly and in a targeted manner.
Make sure your Entra ID environment is secure and users are protected. Check the security protocols continuously and systematically!
Stay safe - and be prepared!
Sources:
[Source1] Entra ID: Microsoft sperrt nach Logging-Panne Nutzer aus – Golem.de


hi
Hello 😉