It's no secret: cyberattacks are becoming more frequent and more sophisticated. But even the simplest techniques often lead the attackers to success. After all, the weakest link in the defense against cyber attacks is the human being. In this post, I show how you can protect Azure Active Directory (AAD) identities with the right MFA method without neglecting the human factor. Not only is the security aspect important to consider, but also user acceptance.
Not all MFAs are the same
People who use IT applications are already used to multi-factor authentication (MFA). Be it in a professional environment, but also in private life. The best and most tangible example is probably online banking. But not every MFA method has the same security factor.
SMS & calls as an unsafe MFA method
Certainly better than nothing, but SMS and calls in particular are considered an unsafe MFA method. The main reasons for this are...
- SMS and voice calls are not encrypted.
- SMS codes are vulnerable to phishing.
- Attackers trick employees of telephone companies.
- Provider outages.
- SMS as an old technology will not or hardly become more secure in the future.
If you want to know more about each of these, Tom Merritt has described them briefly and clearly on TechRepublic at this link.
Using the Authenticator App
In the professional environment, more and more users are getting used to the Authenticator app. There, either a token code is displayed, which has to be entered, or a push notification is displayed to approve the authentication process.

This method is considered much more secure because it is tied to the specific device with the registered and approved Authenticator app. With the SMS and token code variant via Authenticator app, the user experience is roughly the same. With both variants, a code must be read and entered manually from the phone. However, since the user experience with push notification is much better and meets with greater acceptance on the part of the users, this is the preferred option. Despite significantly increased security compared to the SMS method, this method is also vulnerable. For such an attack, the attackers use social engineering methods. For example, MFA fatigue, also called MFA bombing or similar, as shown by the example of the successful attack on Uber in September 2022. The human factor is once again at the center here and probably the biggest weakness of the system.
Number matching
This method combines the advantages of the token code method and push notification. Furthermore, it efficiently protects against MFA fatigue and impresses with its simplicity and ease of use. The number matching method displays a two-digit number to the user on the login screen and simultaneously receives a push notification in their Authenticator app. The user now has to enter and confirm the number in the Authenticator app in reverse to the token code method. Details on this method and how you can set it up are described in the article Number Matching MFA Rollout.
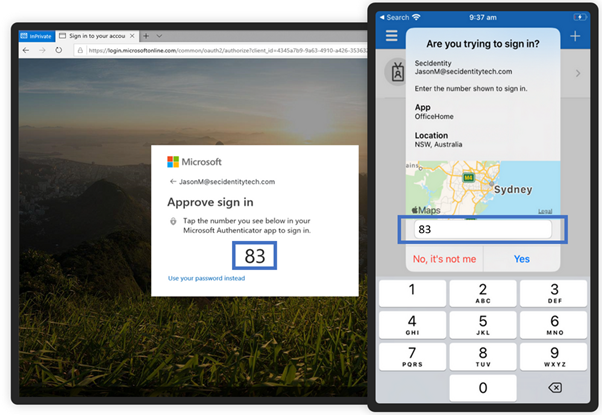
Source: https://learn.microsoft.com
FIDO2 and smart cards
FIDO2 tokens and smartcards are two MFA methods that are steadily gaining popularity due to their high security and ease of use. One of the main advantages of using FIDO2 tokens and smartcards is that they provide strong cryptographic security. These devices store cryptographic keys that are used to authenticate the user, making it difficult for attackers to gain unauthorized access. They are considered the most secure MFA methods and are also "Unphishable". They are therefore also effective protection against social engineering.
Another advantage of FIDO2 tokens and smartcards is their ease of use. Once the device is registered with the user's account, authentication can be completed with a simple tap or touch. This is even more convenient than other MFA methods that require the user to enter a code. However, the high initial cost due to the necessary hardware procurement is a drawback.
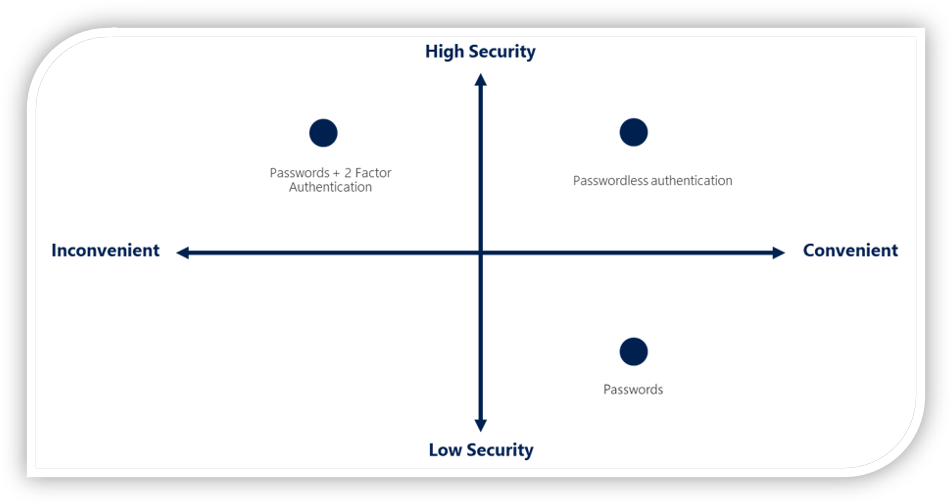
Passwordless authentication
Microsoft's Passwordless Authentication is a new authentication method that is gaining popularity. Users no longer need to enter a password to log in to their account. Instead, other factors such as the previously discussed MFA methods like FIDO2, smart cards, or the Microsoft Authenticator app are used to verify the user's identity.
Compared to the use of a password, passwordless authentication offers several advantages.
- Increased safety: Next to humans, passwords are often the weakest link in the security chain, as they can be easily compromised by phishing attacks or brute force attacks. Passwordless authentication eliminates the risk of password-based attacks and provides a higher level of security for user accounts.
- Better user experience: With passwordless authentication, users can easily and quickly authenticate with a biometric scan or by simply tapping a security key or the Microsoft Authenticator app. This can lead to a more seamless and convenient user experience and increases adoption.
- Cost savings: Resetting passwords and locking accounts can be time-consuming and costly for IT departments. Passwordless authentication eliminates these issues, reducing IT support costs and increasing productivity.
- Improved compliance: Many industries have strict compliance regulations that require strong authentication methods. Passwordless authentication can help organizations meet these compliance requirements and avoid penalties for non-compliance.
- Reduced risk of data breaches: Passwords can be easily stolen or hacked, which can lead to a data breach. Passwordless authentication eliminates this risk, reducing the likelihood of a data breach and the associated costs and reputational damage.
Some of the advantages listed also apply to authentication by password in combination with MFA methods. In summary, however, it can be said that passwordless authentication offers greatly improved usability, while the security of the MFA method is not sacrificed.
Human factor and acceptance
As is made clear throughout this article, the human factor, as well as acceptance, must be considered for all methods. For example, if users are repeatedly asked to provide multiple forms of identification (MFA), this can be frustrating and time-consuming. This can lead to user resistance and also indifference, which weakens the overall security of the system. MFA methods should therefore be as simple as possible while still providing the necessary security.
Another important aspect is acceptance. Users must understand the importance of MFA and be willing to use it. Internal communication and training therefore play a central role in the successful rollout of MFA. This is the only way to ensure that users see MFA not as an obstacle, but as protection. As a side effect, the initiative will then automatically meet with less resistance. However, which method can be chosen and meets with the corresponding acceptance depends on various factors. The following are a few examples of questions that should be asked.
- Protection value: How worthy of protection are my data and systems and what am I willing to do and pay for protection?
- Digital skills of employees: Do my employees, customers and partners have the skills to successfully apply the chosen MFA method?
- Training and communication: How do I want to inform employees, customers and partners about the introduction? What education or training may be necessary?
- Legal: Am I allowed to force users to use a certain MFA method? For example, when choosing the Authenticator app if the smartphones required for this do not belong to the company but are private?
- Necessary hardware: Do all those involved have the appropriate hardware? For example, when choosing the Authenticator app, everyone must have a smartphone. Often forgotten but not to be neglected are external parties, customers and partners who have to authenticate themselves via MFA.
- Protection and handling: How can I best protect the enterprise, but not unnecessarily burden the user with complex authentication processes?
Conclusion
Several methods exist to successfully protect Azure Active Directory (AAD) identities without neglecting the human factor. Although multi-factor authentication (MFA) is considered more secure than traditional authentication methods, not every MFA method is equally secure. It is recommended to use the Authenticator app or methods such as number matching, FIDO2 tokens, and smart cards to ensure higher security and ease of use. Moreover, it is not only important to consider the technical aspect of security, but also the culture and acceptance of users to increase the effectiveness of security measures. In my opinion, the future of secure authentication belongs to passwordless authentication using FIDO2, smart card, Windows Hello for Business or number matching in the Authenticator app.



Hoi Yannic
Sehr gut auf den Punkt gebracht!
Wirklich schöner Post. 🙂
Was sind so deine Favoriten, welche Du für FIDO2 empfehlen kannst? (Bspw. Preis / Leistung oder Erfahrungen)
Hallo Cedric
Schön, dass er dir gefällt. Oft sind Smartcards im Einsatz, weil diese bspw. für andere Systeme bereits vorhanden sind. Das ist dann natürlich das Kosteneffektivste. Für neue Setups preist Microsoft selbst Yubikeys von Yubico an. Dazu habe ich ebenfalls einen Post geplant und hoffe, dass ich diesen bald veröffentlichen kann.
Grüsse