This blog post explains how to set up Azure Multi-Factor Authentication for your On-Premises Remote Desktop Service (RDS) environment. The blog post is intended for understanding and shows the most important steps for preparation as a step-by-step guide.
Multi-factor authentication
The concept of Multi-Factor Authentication (MFA) is already very common and highly regarded today. Such an authentication consists of several components, not only username and password. Typically these are...
- Something you know (password)
- Something you own (a trusted device, e.g. smartphone)
- Something you are (fingerprint, face recognition, etc.)
The risk of unauthorized access is minimized many times over with the advanced factors of authentication. The Microsoft product Azure Multi-Factor Authentication offers exactly these possibilities, both for cloud and their on-premises services. This article focuses on the integration of Azure Multi-Factor Authentication into an existing Remote Desktop Service (RDS) environment. Translated with www.DeepL.com/Translator (free version)
Initial situation & requirements
To use Azure MFA for the existing RDS environment, there are a handful of requirements:
- Synchronization of the Onsite Active Directory and Azure Active Directory
- At least two Windows Server 2008 R2 servers or newer with the Network Policy and Access Services (NPS) role installed - for example, on the Remote Desktop Gateway and Azure Active Directory Connect (AADC) or another server in the domain
- Licenses for Azure MFA - This can be done e.g. with Azure AD Premium or another license plan containing Azure MFA . <The consumption-based license for Azure MFA is not compatible with NPS.
The following chapters assume that the prerequisites are met, the synchronization of the directories is already configured, an existing RDS infrastructure exists and the NPS role is installed on two servers.
Authentication method with Azure MFA
By integrating Azure Multi-Factor Authentication into the existing RDS solution, the authentication process extends into the Microsoft cloud. The advantages of MFA are thus available. The procedure is structured as follows:
- The Remote Desktop Gateway receives the authentication request and forwards it to the server on which the NPS extension is installed. From NPS the request is forwarded to DC.
- The DC checks the login information and reports the result back to the NPS.
- If the result is positive, the NPS triggers a request to Azure Active Directory for further authentication.
- The Multi-Factor Authentication is requested by the Azure Active Directory using one of the supported and configured options (push notification, call, SMS, code, ...) and the result is sent to the NPS if successful.
- The NPS server sends the message of successful authentication to the RDS, which grants access to the user authenticated via MFA.

Azure MFA Configuration
Before the NPS extension can be installed and used, MFA must be set up for the Azure accounts. For the setup to work, at least one user must be successfully registered for Azure MFA . To achieve this the user has to log in at https://aka.ms/mfasetup. The user can then configure his desired authentication method, e.g. via token or Authenticator App.
Somit ist die Vorarbeit bereits geleistet. Die Conditional Access Policy ist bei der NPS Konfiguration und Authentifizierung nicht berücksichtigt. Daher ist die Einrichtung einer solchen nicht notwendig. Ist der NPS Server korrekt konfiguriert, muss sich jeder User nach der Authentifizierung über den NPS Server zusätzlich mittels MFA authetifizieren. Ist Azure MFA für einen User nicht konfiguriert, so kann der User die zusätzliche Authentifizierung nicht durchführen. Der Benutzer wird dadurch abgelehnt. Für Testzwecke gibt es aber eine Möglichkeit dies zu umgehen. Dafür muss man aber erst die NPS Erweiterung installieren. Diese Möglichkeit ist daher im Folgekapitel als «Optional» aufgeführt.
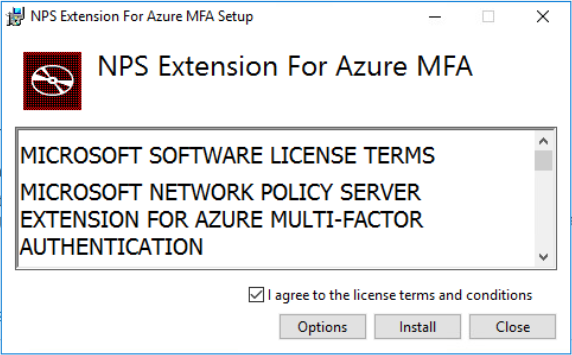
Installation and Configuration NPS Extension
For successful setup, the NPS extension is started on the NPS server. For this purpose the extension can be downloaded from this link on the NPS server. Then, the NpsExtnForAzureMfaInstaller.exe is executed and installed.
CAUTION: The NPS extension must NEVER be installed on the RD gateway server.
Optional:
If a certain registry key is available, the NPS server does not require every user to authenticate via MFA. It is important to understand that this option is a security vulnerability. Therefore, the option should only be configured for testing during implementation to avoid a limitation of the existing operation.
For configuration, only the registry key HKLM\Software\Microsoft\AzureMFA\REQUIRE_USER_MATCH must be set from TRUE to FALSE. This key controls what should happen to users who are not registered for MFA . The values mean the following.
| Value | User MFA Status | Effect |
|---|---|---|
| Der key existiert nicht | Nicht registriert | MFA ist nicht erforderlich |
| TRUE | Nicht registriert | MFA ist nicht erforderlich |
| FALSE | Nicht registriert | Authentifizierung ohne MFA |
| FALSE | Registriert | Authzentifizierung mit MFA erforderlich |
| TRUE | Registriert | Authentifizierung mit MFA erforderlich |
Self-signed certificate
Nachdem die Erweiterung installiert wurde, wird ein Zertifikat benötigt. Die heruntergeladene Erweiterung enthält ein PowerShell Skript, welches direkt ein selbstsigniertes Zertifikat erstellt, speichert und installiert. Das Skript erstellt im Azure AD zudem ein Dienstprinzipal. Dieses Prinzipal wird dem Zertifikat anschliessend automatisch zugeordnet. Weiter gewährt das Skript dem «NETWORK SERVICE» Zugriff auf das neu erstellte Zertifikat.
Das Skript lässt sich wie folgt finden:
C:\Program Files\Microsoft\AzureMfa\Config\AzureMfaNpsExtnConfigSetup
ACHTUNG: Bei Servern in deutscher Sprache (nicht empfehlenswert), muss das Skript zuerst noch editiert werden, da das deutsche System keinen «NETWORK SERVICE» kennt. Der «NETWORK SERVICE» muss entsprechend im Skript mit dem deutschen Äquivalent ersetzt werden (Netzwerkdienst).
The script then prompts you to log in to the Azure Active Directory with an Azure AD Admin . If the authentication is successful, the script asks for the Tenant ID. This can be found in the Azure Portal by navigating to Azure Active Directory >> Properties Navigate and copying the value under Directory ID .
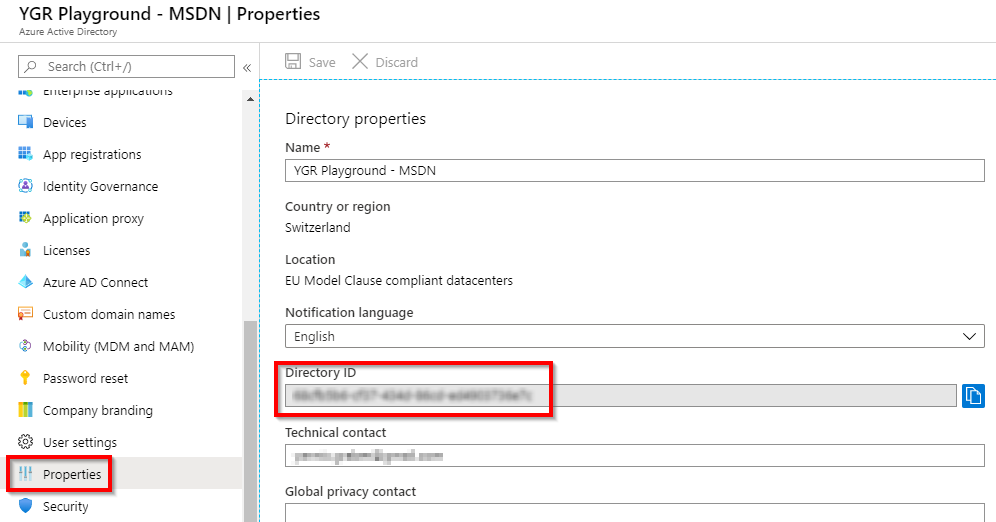
Diese ID muss im Skript angegeben werden um die Verbindung zum Azure Active Directory herzustellen. Mit «Enter» bestätigt, erstellt das Skript das selbstsignierte Zertifikat und es kann mit dem nächsten Schritt fortgefahren werden.
You can then continue with the configuration. A step-by-step guide from Microsoft already exists for this. The configuration should be carried out in the following order.
- Konfigurieren von NPS-Komponenten auf dem Remotedesktopgateway
- Konfigurieren von NPS auf dem Server, auf dem die NPS extension installiert wurde
- Checking the configuration
After these configurations have been made, Azure MFA is successfully integrated into the existing RDS environment.
Good to know - Summary
- To configure an RDS environment with Azure MFA , it requires at least two servers. One server is required as RDS gateway with installed NPS role , the other as another NPS server on which the NPS extension is installed. The extension must NOT be installed on the RDS gateway .
- Defined Conditional Access Policies in Azure AD are NOT considered in the Azure MFA integration using NPS .
Sources: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension-rdg https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension