The work forms "home office", "remote work" or even "work anywhere" are becoming increasingly important, especially in recent months. This change affects not only users, but also IT staff and system administrators. However, I am often confronted with mistrust and security concerns when dealing with such issues. This is where Azure Bastion comes into play. Bastion not only enables "work anywhere" for system administrators, but also provides increased security and secure access to your Azure VMs without the need for a VPN!
Principle and key facts of Azure Bastion
In principle, Azure Bastion can be described as "Jump host as a Service". However, since Bastion is a PaaS ("Platform as a Service") offering, the administrator does not need to connect to it first, as would be the case with a classic "Jump host". The administrator can conveniently and centrally select the desired server in the Azure Portal and connect via Bastion, as the picture shows.
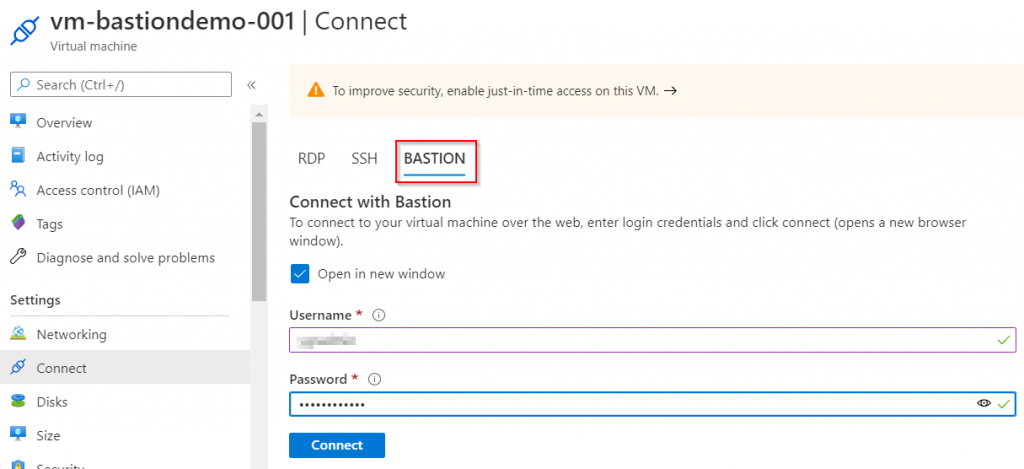
The central access is very useful. In my opinion, the main benefit is that the servers do not need a public IP thanks to Bastion and connects via TLS and therefore encrypted. So thanks to Azure Bastion port 443 is the only port you have to publish outside the network. Ports for RDP and SSH are only necessary internally. The following picture and the following description shows how the access via Azure Bastion works.
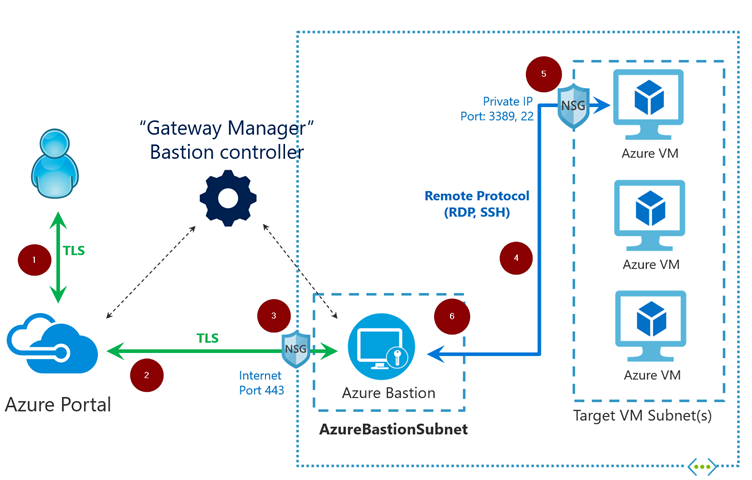
- The administrator connects to the Azure Portal via TLS and selects the desired server to access.
- Azure forwards the traffic to the Bastion Service ("Jump host as a Service"), also via TLS.
- With the upstream Network Security Group (NSG), only port 443 must be open.
- Bastion establishes the SSH / RDP connection with the desired VM.
- You can restrict the NSG in front of the subnet or VM so that the NSG allows SSH and RDP only from the Azure Bastion.
- The session is then made available to the administrator via HTML5.
Properties of Azure Bastion
The above description has already brought to light some features and one or two advantages of Azure Bastion, but there are more. There are (still) some disadvantages and limitations, which I would like to point out as well.
Advantages
The following list shows advantages and positive characteristics of Azure Bastion.
- VM and Network Security
Azure Bastion contributes to VM and network security while enabling the "work anywhere" principle for system administrators. Because an administrator must first identify with Azure, you can also make use of services such as conditional access, just-in-time access and more. - No VPN necessary
Access via Azure Bastion works via port 443 and HTML5. It is therefore not necessary to have a VPN. But you can configure this yourself if you have security concerns. - No public IP for VMs
The VMs do not require a public IP because they are accessed via the private IP of Azure Bastion. The communication between Bastion and VM takes place in the internal VNET. - Protection against port scanning
Because VMs do not require a public IP and Azure Bastion only uses port 443, port scanning from outside the private network is blocked. - Port restriction on internal NSG (Personal recommendation) The Network Security Group can be configured to allow RDP and SSH only from Azure Bastion. This serves as further protection if someone has already entered the network, so that the VMs cannot be accessed without authorization even from inside the network.
- Secure and seamless RDP and SSH connection via TLS
You can access your VMs directly in the Azure Portal. The SSH or RDP session is made available to you in encrypted form via TLS. - No RDP or SSH client required
No additional software or clients are required for the connection. The session is provided directly as HTML5 without the need to install anything else. - No agent on VM necessary
You do not need to install an agent on the VMs you want to access via Bastion. - Scaling - One bastion per network
For a whole Azure VNET you only need one Azure Bastion. If you have placed Bastion in a network, you can use it for all the VMs it contains. - Fully managed service
Azure Bastion is a "platform as a service" offer. This means that the service is maintained and kept up-to-date by Microsoft. You don't need to worry about maintenance and system hardening, unlike a traditional "jump host". - Simple and fast implementation
Creating your own Azure Bastion takes only a short time. How you can create one is described in a other post here. Nevertheless, it is important that you do the conceptual groundwork beforehand.
Disadvantages
The following list shows the disadvantages and negative characteristics of Azure Bastion at the time of writing this blog post
- IPv6 is not supported
Unfortunately only IPv4 is currently supported, not IPv6. - Copying of files is not possible
Also copying files to or from a remote session is not supported. However, it can be assumed that Microsoft will come up with something for this. Copy-paste is also possible. - access to VMs in "Spoke" networks not possible
The "Hub & Spoke" network architecture is widely used and is considered best practice on Azure. Unfortunately, at this time, only VMs on the same network can be accessed from an Azure bastion on the hub network. All VMs in a spoke network cannot be accessed from this Azure bastion. Currently, one Azure Bastion per network must be implemented, which results in corresponding costs. Microsoft is aware of this, however, and has already announced via customer feedback that it would like to support "Hub & Spoke" architectures with Bastion in the future and is working on it (see here).
Conclusion
Azure Bastion is a service that, with the right configuration, can make a significant contribution to network security. I am particularly impressed by the simplicity of the platform service, both in implementation and operation. For administrators and specialists, who already use the Azure Portal on a daily basis, Azure Bastion is no additional obstacle in terms of usability and at the same time protects against various dangers. However, the fact that the network architecture "Hub & Spoke" is not yet supported is unfortunate, especially since this architecture is best practice and is practiced in many places. If this hurdle is overcome, Azure Bastion is an excellent service for both SMEs and enterprises. Azure Bastion provides secure access to your Azure VMs at an affordable price of approximately USD 140 per month (excluding traffic).
Sources:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
https://docs.microsoft.com/en-us/azure/bastion/bastion-create-host-portal